OCSPs, Timestamps, CRLs, and certificate data need to be embedded into a PDF to ensure long-term digital signature validation. This approach is called PAdES LTV or, in eIDAS terminology, PAdES-BASELINE-LT.
Previous Work: From PAdES-T to PAdES-LT
In a previous post, we covered how to create a PAdES signature from scratch by generating an ETSI.CAdES.detached and embedding it into the ByteRange
That method produces a valid PAdES-BASELINE-T, even though the embedded CAdES signature itself can be CAdES-BASELINE-LT.
What You Need for Long-Term Validation (LTV)
To upgrade a PDF signature to PAdES LTV, you must add a Document Security Store (DSS) and optionally a Validation Related Information (VRI) dictionary. By embedding certificates, OCSP responses, and CRLs at the time of signing, the PDF remains verifiable in the future—even if signer certificates expire or OCSP responders go offline.
Don’t Forget the Timestamp
Including a timestamp is mandatory. If your CAdES signature already includes it, you’re good. If not, you’ll need to apply one separately on the PDF.
DSS vs VRI – What to Use?
While both DSS and VRI hold similar information, ETSI EN 319 142-1 advises against using VRI:
“The VRI dictionary should not be used. The inclusion of VRI dictionary entries is optional. All validation material referenced in VRI entries is also referenced in DSS entries.”
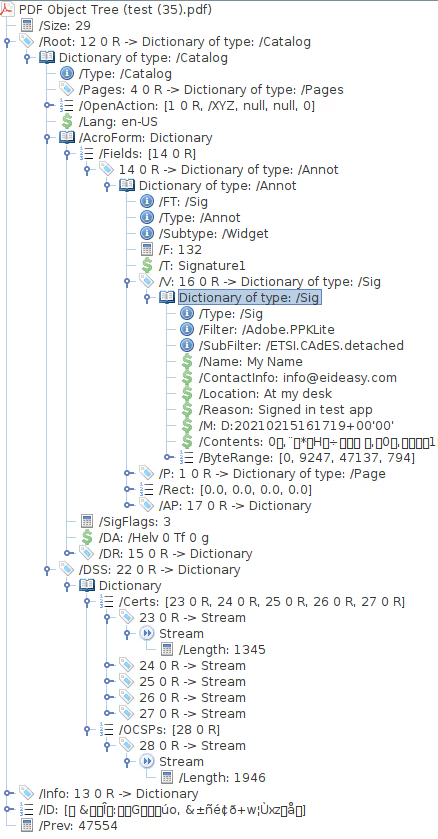
Example: PAdES-BASELINE-LT Structure
Here’s an example of a PDF tree structure containing a DSS entry that supports a valid PAdES-BASELINE-LT with a Qualified Electronic Signature (QES).
How to Create the DSS Section
- Sign the PDF as usual.
- In the incremental update, add the DSS dictionary.
- Collect and insert:
- Signer certificate
- CA certificate
- OCSP responder certificate
- Timestamp server certificate
Place these into theCertsarray of the DSS.
- Add all OCSP responses and CRLs to the appropriate arrays inside the DSS dictionary.
Tools and Implementation Tips
You’ll need a PDF editing library to manage this. In Java, PDFBox can be used.
If you're an experienced cryptography developer, the steps above should be enough to guide your implementation.
Need Help?
If you need expert help building secure and standards-compliant PDF digital signature workflows, contact the team at eID Easy via info@eideasy.com.